What is Access Control?
The purpose of access control is to grant entrance to a building or office only to those that are authorized to be there. The deadbolt lock, along side its matching brass key, was the gold standard of access control for several years; however, modern businesses want more. Yes, they need to regulate who passes through their doors, but they also need a thanks to monitor and manage access. Keys have now passed the baton to computer-based electronic access control systems that provide quick, convenient access to authorized persons while denying access to unauthorized ones.
Access Control Components
Access control systems aim to regulate who has access to a building, facility, or a “for authorized persons only” area. this is often typically administered by assigning employees, executives, freelancers, and vendors to differing types of groups or access levels. Everyone could also be ready to use their access cards to enter the most door, but not be ready to access areas containing secure or privileged information.
For clarity, we divide the components into three groups: user-facing components, admin-facing components, and infrastructure components. Let’s dive into the nuances of the three categories.
User facing:- The most familiar parts of access control systems are the cards, ID badges, and, more recently, the smartphone apps that elicit an OK beep when presented at a card reader and unlock the door. These also are referred to as credentials, since they bear the user’s data that tells the reader to grant you permission to get on the premise, or in other words, that you simply are a licensed entrant.
Access cards are typically proximity cards that, instead of being swiped or inserted like credit cards, are held two to 6 inches ahead of the cardboard reader. an equivalent procedure is followed for phone apps. The advantage of using credentials is that they’re personalized, so any unlock event are often traced back to the person related to it.
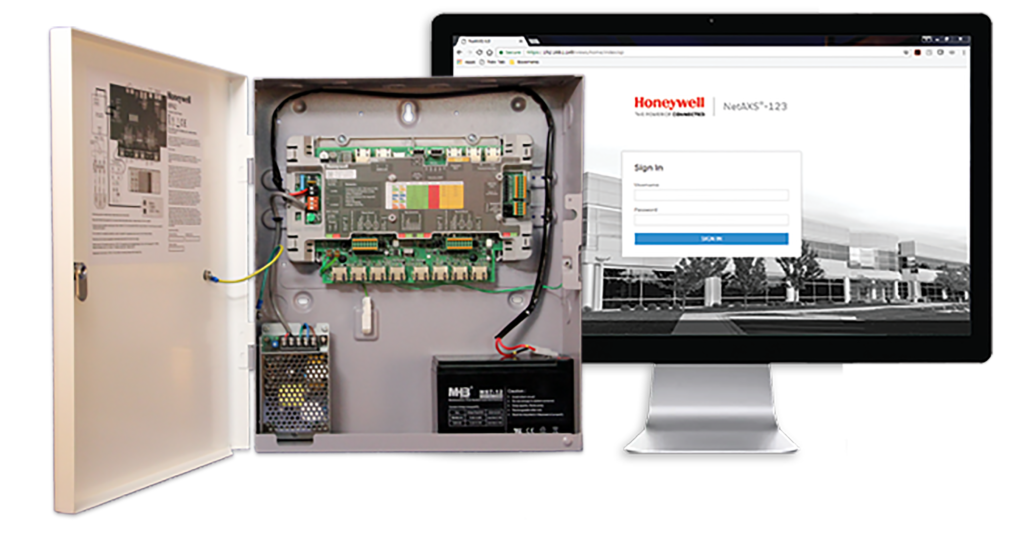
Admin facing:- The admin-facing side is that the management dashboard, or portal, where the office administrator, head of security, or IT manager sets the parameters of persons allowed to access the premises and under which circumstances they will do so. This involves a management dashboard, often within the cloud, and how to provision access—such as a card programming device.
In more advanced systems, the manual operations aspect are often automated. for instance , the provisioning (creating and deleting access) are often done automatically by connecting the access dashboard to the corporate directory of employees. When a replacement hire shows up within the system, new access is automatically positioned via an API or integrating database service like Google Apps, Microsoft Azure, SAML, or Okta.
Infrastructure:- The infrastructure components are those that believe your building infrastructure so as to function. the foremost obvious parts are locks, but there are other components, like the controller, server, and cables.




